Mitigating a brute-force login attack via telnet backdoor
I have a VPS through Linode that I use to host dozens of websites (including this one). Securing your server against brute-force login attempts is one of the first steps you should take when setting up a new server, and Linode details this fairly well.
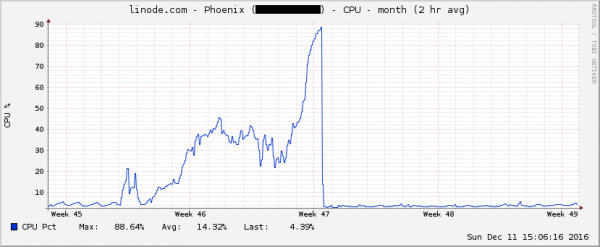
However, one day I was surprised to notice that my CPU usage, though steady, was hovering at close to 90%. A peek at the historical usage showed this this had been increasing steadily for over a week now, but went under the radar.
A look at top revealed accounts-daemon (the service that handles user authentication) to be the culprit, and my /var/log/wvmb file (which logs failed logins) was draining my available disk space to nearly nothing.
Okay, easy enough. Let’s cut off SSH access until I have time to figure out why the usual defenses weren’t working. However, the attack continued. How could this be?
Turns out the attack was happening with an old authentication method called telnet. Every article I read about telnet suggested using SSH instead for its superior security when authenticating yourself, but I couldn’t find any resources about securing telnet against malicious login attempts.
I was able to successfully mitigate the attack by turning off telnet authentication completely. In my case, I commented out this line in /etc/inetd.conf:
telnet stream tcp nowait root /usr/sbin/tcpd /usr/sbin/in.telnetd
Next: An interview with the “Brains On!” science podcast
About Me
Hi, I'm Neil! I'm passionate about building delightful products at scale, creating music, and performing in theatre and comedy shows.

Leave a Comment